Introduction
Phishing attacks are among the most pervasive and damaging forms of cybercrime today. With just a single click on a malicious link or attachment, an unsuspecting user can inadvertently give attackers access to sensitive information, leading to data breaches, financial loss, and reputational damage. As phishing tactics become increasingly sophisticated, it’s more important than ever to know how to recognize and defend against these threats.
In this post, we’ll explore the different types of phishing attacks, how they work, and the best practices for protecting yourself and your organization from falling victim to these schemes.
Understanding Phishing Attacks
Phishing is a type of social engineering attack where cybercriminals deceive individuals into revealing confidential information, such as login credentials, credit card numbers, or other personal data. These attacks typically come in the form of emails, but they can also occur via text messages (smishing), phone calls (vishing), or even social media.
Common Types of Phishing Attacks
- Email Phishing: The most prevalent form, where attackers send emails that appear to come from legitimate sources, tricking recipients into clicking on malicious links or downloading harmful attachments.
- Spear Phishing: A more targeted form of phishing, where attackers tailor their messages to a specific individual or organization, often using information gathered from social media or other online sources to make the email appear more credible.
- Clone Phishing: Attackers create a near-identical copy of a legitimate email that the victim has previously received, replacing legitimate links or attachments with malicious ones.
- Whaling: A form of phishing that targets high-profile individuals, such as executives or government officials, with the goal of gaining access to sensitive information or high-value assets.
How Phishing Attacks Work
Phishing attacks often rely on psychological manipulation, preying on human emotions such as fear, curiosity, or urgency. Here’s a typical process of how a phishing attack unfolds:
- The Setup: The attacker creates a convincing email, text message, or other forms of communication that mimics a trusted entity, such as a bank, social media platform, or a well-known company.
- The Hook: The message includes a call to action—such as clicking on a link, downloading an attachment, or providing personal information—often under the guise of resolving an issue or receiving a reward.
- The Attack: If the victim follows the instructions, they may be redirected to a fake website designed to steal their credentials, or their device may be infected with malware that grants the attacker access to their systems.
- The Exploitation: Once the attacker has obtained the victim’s information, they can use it to commit fraud, steal sensitive data, or gain unauthorized access to networks and systems.
Defending Against Phishing Attacks
1. Be Skeptical of Unsolicited Messages
Always be cautious when receiving unexpected emails or messages, especially those that request sensitive information or prompt you to click on links. If something seems off, it probably is.
2. Verify the Source
Before clicking on any link or downloading an attachment, verify the sender’s email address and scrutinize the content of the message. Legitimate organizations will never ask for sensitive information through insecure channels like email.
3. Look for Red Flags
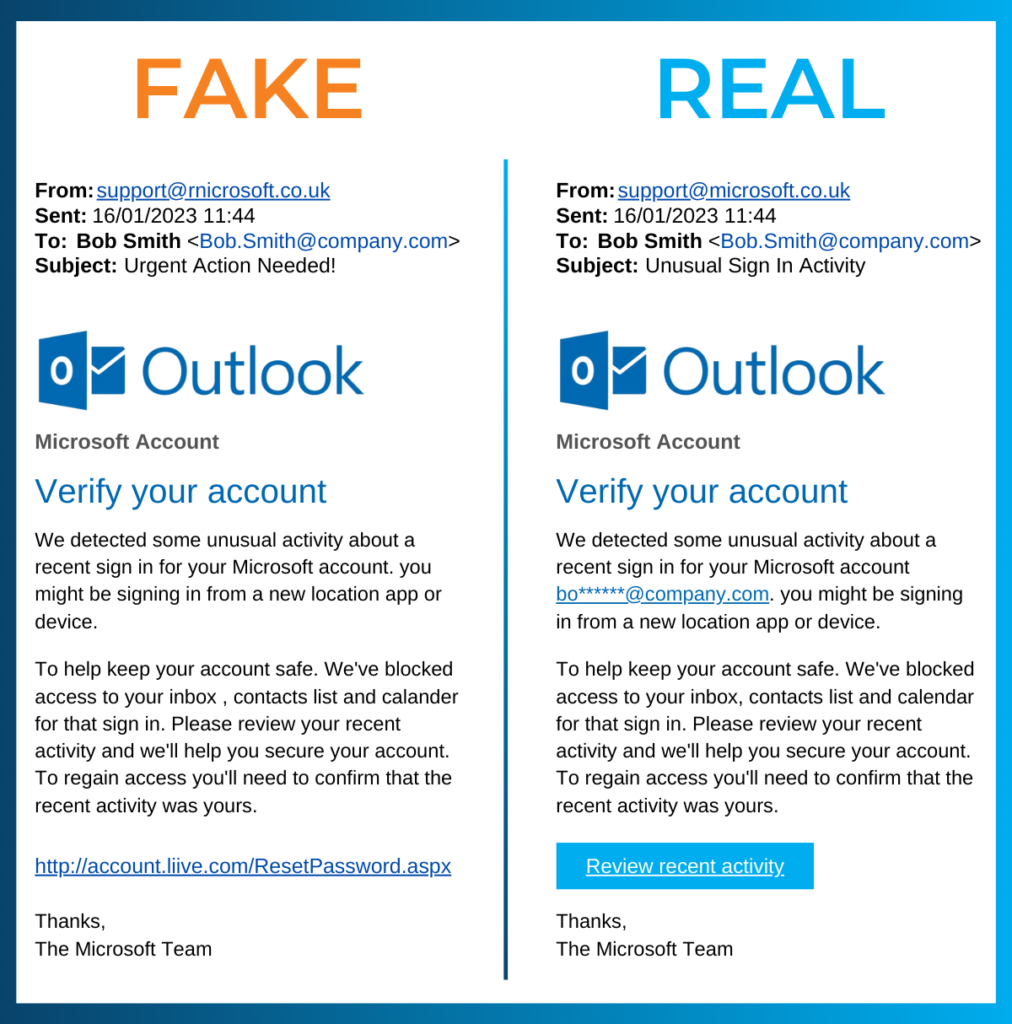
Phishing emails often contain subtle red flags, such as poor grammar, generic greetings (e.g., “Dear Customer”), and mismatched URLs. Hover over links to see where they lead before clicking.
4. Enable Multi-Factor Authentication (MFA)
Even if attackers manage to steal your credentials, multi-factor authentication adds an extra layer of security, making it much harder for them to gain access to your accounts.
5. Regular Security Awareness Training
Conduct ongoing security awareness training for employees to educate them on the latest phishing techniques and how to spot suspicious activity. Simulated phishing exercises can also help reinforce this training.
6. Use Advanced Email Filters
Deploy advanced email filtering solutions that can detect and block phishing emails before they reach your inbox. These tools can analyze the content of emails, identify suspicious links, and filter out potential threats.
What to Do If You Suspect a Phishing Attack
If you believe you’ve received a phishing email or fallen victim to a phishing attack, take the following steps immediately:
- Do Not Click or Respond: If you suspect an email is phishing, do not click any links, download attachments, or respond to the message.
- Report It: Forward the email to your IT or security team for further analysis. Many companies also have a process for reporting phishing attempts.
- Change Your Passwords: If you’ve already clicked on a link or provided information, change your passwords immediately and enable MFA on your accounts.
- Monitor Your Accounts: Keep a close eye on your financial and online accounts for any unusual activity. Notify your bank or credit card company if you notice any unauthorized transactions.
Conclusion
Phishing attacks continue to be a significant threat to individuals and organizations alike, but by staying informed and vigilant, you can reduce the risk of falling victim to these schemes. Remember to scrutinize unexpected messages, verify the source before taking any action, and regularly educate yourself and your team on the latest phishing tactics.
Stay safe online, and continue following InfoSec Nook for more tips, insights, and best practices to keep your digital world secure.

No responses yet